Microsoft Defender VS CrowdStrike EDR: A Hybrid Approach for Cost-Effective Enterprise Security
Why choosing one product is no longer the only answer. A pragmatic hybrid model that balances protection, visibility and cost.
SECURITY
Hangman
10/27/20254 min read


Introduction
Many organisations instinctively compare Microsoft Defender and CrowdStrike Falcon as if they were mutually exclusive choices. Both products are Gartner Leaders and each brings distinct strengths: CrowdStrike excels at lightweight endpoint sensor performance and AI-driven breach prevention; Microsoft Defender offers broad cross-domain XDR coverage across endpoints, email and cloud. Rather than asking which is strictly "better", a practical and cost‑sensitive question is: Can both run together to deliver complementary security benefits?
This post explains a recommended hybrid deployment that leverages existing Microsoft 365 E5 investments (Defender for Endpoint Plan 2 included) while selectively deploying CrowdStrike Falcon where it gives most value. The result is improved detection, richer telemetry for SOC use-cases, and stronger protection for high‑value assets without excessive extra spend.
Why organisations hesitate to use Defender alone or CrowdStrike alone
Microsoft Defender concerns: objections are often not about detection capability but about vendor consolidation — Defender is both the OS maker and EDR vendor. This creates perceived conflict-of-interest for some customers who worry about impartial detection or independent telemetry.
CrowdStrike limitations: excellent at endpoint protection and EDR but may lack native visibility into Microsoft cloud services (Exchange Online, SharePoint, Teams, Entra ID) and email telemetry that are necessary for end‑to‑end XDR use cases.
Each product fills gaps left by the other. Combining them yields better overall coverage.
The hybrid model we recommend (straightforward and cost effective)
Keep Microsoft Defender P2 as the baseline for all endpoints (leveraging M365 E5). Deploy CrowdStrike Falcon sensor selectively to servers, IT staff, and other VIP/high‑value targets.
Why this allocation works:
Cost efficiency: organisations with M365 E5 already have Defender P2 entitlement — using it as default minimises incremental software spend.
Risk prioritisation: CrowdStrike on servers and VIPs protects the most valuable and exposed assets with a lightweight, high‑performance sensor and strong breach prevention.
Telemetry synergy: Defender covers cloud and email telemetry while Falcon provides superior endpoint detection for critical hosts. Together they feed the SOC richer signals.
Concrete example:
All corporate laptops and general staff: Defender for Endpoint P2 (native with M365 E5).
Domain controllers, database servers, critical app servers, SOC analyst workstations, C‑suite laptops: CrowdStrike Falcon sensor + Defender (Defender on these can remain enabled for telemetry; Falcon becomes primary EDR for response/containment on these hosts).
Operational benefits for the SOC and enterprise security posture
Layered detection and prevention: CrowdStrike's AI + Falcon sensor serves as a strong first line of defence for VIPs and servers while Defender provides broad XDR coverage and cloud context.
Improved visibility: Falcon Discover and Defender for Cloud/Office telemetry together give SOC teams better environment discovery, account activity, and cloud events.
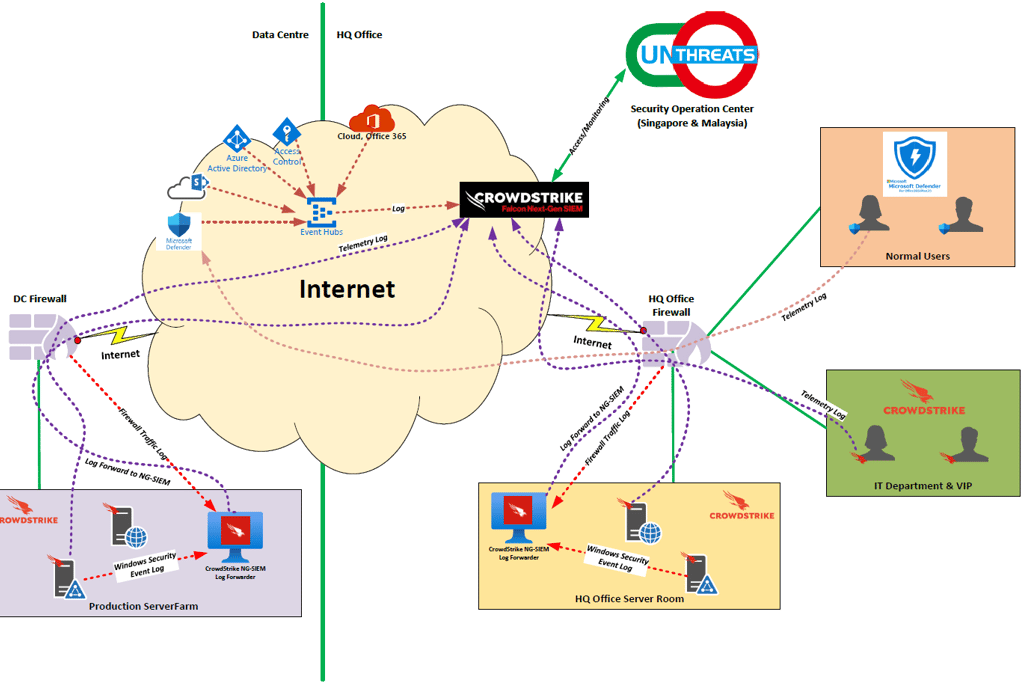
Richer SIEM correlation: Sending Defender and Falcon telemetry to a Next‑Gen SIEM (NG‑SIEM) provides correlation across endpoint, email, cloud, firewall, and network logs for advanced detection rules, incident response and threat hunting.
Cost‑effective compliance: This hybrid architecture satisfies many enterprise security controls without requiring every endpoint to run a paid third‑party agent.
Logs and network considerations (how to complete coverage)
To maximise detection and intrusion‑surface coverage, forward the following to NG‑SIEM:
Firewall logs (perimeter and inter‑VLAN traffic)
Server Windows Security event logs and syslog from hosts
Network appliance and IDS/IPS logs
Defender for Cloud and Defender for Endpoint telemetry
CrowdStrike Falcon telemetry (events, detections, process trees)
Entra ID / Azure AD sign‑in and conditional access logs
Example outcome: If user and server VLANs terminate at a firewall and firewall logs are ingested, the NG‑SIEM can detect unusual east‑west traffic patterns and act as an NDR‑like capability for lateral movement detection.
Use cases and SIEM detection rules enabled by hybrid visibility
Mass download from cloud storage: Defender for Cloud and Office telemetry show bulk file downloads; NG‑SIEM correlates this with endpoint events (Falcon) to identify exfiltration.
Impossible travel / anomalous sign‑ins: Entra ID logs combined with endpoint telemetry allow SOC to detect impossible travel and trigger conditional access or investigation workflow.
VPN access controls: When VPN authentication is federated with Entra ID, correlate Entra sign‑in logs with device posture from Defender and Falcon to enforce conditional access and detect suspicious VPN logins.
Practical SOC workflow (how technologies work together)
Alert generation: Falcon detects suspicious process behavior on a critical server; Defender for Cloud reports unusual admin activity in Office 365; Entra ID reports sign‑in from a new country.
Correlation: NG‑SIEM aggregates these events and runs a correlation rule that indicates compromised credentials plus suspicious process execution → elevated incident.
Response: SOC triggers containment then isolate server via Falcon/EDR controls and revoke sessions via Entra ID conditional access; begin IR steps using logs for evidence and forensic artifacts.
This hybrid approach shortens mean‑time‑to‑detect and mean‑time‑to‑respond because the SOC has more independent signals to validate an incident.
Other operational advantages
Decommission redundant log servers: Send logs to SIEM to remove single‑purpose log servers that consume maintenance cost; repurpose the SIEM data for IR, threat hunting and reporting.
Minimise vendor sprawl: The hybrid model uses two strong vendors but keeps infrastructure simple and no need to introduce multiple additional collectors or complex network tap fabrics.
Pragmatic, balanced security
A hybrid MS Defender + CrowdStrike deployment gives organisations the best of both worlds: broad, cloud‑aware XDR from Microsoft plus Falcon’s elite endpoint prevention and lightweight sensor for high‑value assets. For customers already subscribed to M365 E5, this model is highly cost‑efficient. It leverages entitlements while applying CrowdStrike where it matters most.
Contact Pentacraft Innovate for environment assessment and a recommended hybrid Defender + CrowdStrike plan that balances protection, visibility and cost for your organisation.
#crowdstrike #msdefender #singapore #malaysia #edr #soc #mdr #cs #microsoft #microsoftdefender #antivirus #malwareprotection #security #siem #log #ngsiem #threat